Table of Contents
Table of Contents
This chapter gathers general information about IPTables logs analyzer
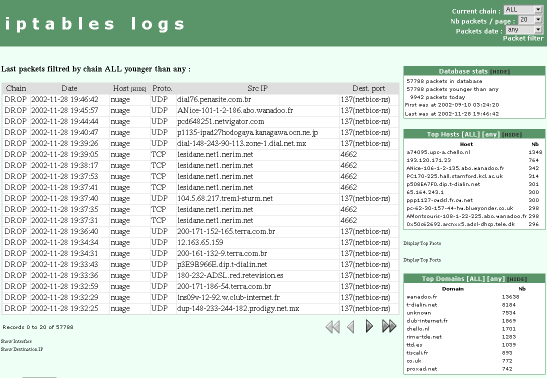
IPTables log analyzer displays Linux 2.4 iptables logs (rejected, accepted, and masqueraded packets) in a nice HTML page. The reports it produces are easy to read and understand, reducing the manual analysis time. They contain statistics on packets and links to more detailed information on a given host, port, or domain.
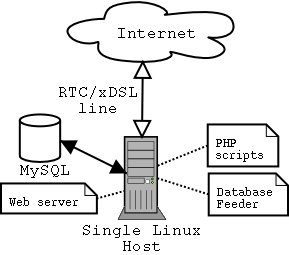
The IPTable Log Analyzer is composed of two different and separate parts :
According to your network architecture, you can run directly the database feeder, the web interface and the database directly on the firewall, but you can chose to use existing hosts of your network as described bellow :
The log analyzer is ready to receive data from different firewalls, so if your network is protected by several firewalls, you can run one database feeder on each firewall and gather information on a single database host.
Table of Contents
This chapter gathers install information about IPTables logs analyzer
Two sources :
Sourceforge based download at http://sourceforge.net/project/showfiles.php?group_id=63361
gege.org website at http://www.gege.org/iptables (main site but slow connection)
start the mysql client (with a user with rights to create databases, here root)
> mysql -u root -p
create the database (here called iptables)
mysql> create database iptables;
grant the mimimun rights to a user used to create the tables and fill the database (here the user iptables_admin will connect from localhost and with password xx)
mysql> grant create,select,insert on iptables.* to iptables_admin@localhost identified by 'xx';
grant select right to a user used by the php interface
mysql> grant select on iptables.* to iptables_user@localhost identified by 'xx'; mysql> grant create temporary tables on iptables.* iptables_user@localhost identified by 'xx';
exit from the mysql client and fill the database with the contents of the file sql/db.sql (in the distribution)
> cat db.sql | mysql -u iptables_admin -p iptables
Add the correct LOG rule to netfilter rules
a rule for logging shall be established for example (to be carefully adapted to your situation) :
iptables -N LOG_DROP iptables -A LOG_DROP -j LOG --log-tcp-options --log-ip-options --log-prefix '[IPTABLES DROP] : ' iptables -A LOG_DROP -j DROP
when you drop packets, you should replace DROP by LOG_DROP for example :
iptables -A INPUT -j LOG_DROP
you should check that the following king of lines apprears in your logs (/var/log/syslog for example) :
Sep 24 21:33:56 nuage kernel: [IPTABLES DROP] : IN=ppp0 OUT= MAC= SRC=62.202.81.132 DST=193.253.186.217 LEN=48 TOS=0x00 PREC=0x00 TTL=111 ID=25302 DF PROTO=TCP SPT=3795 DPT=12345 WINDOW=16384 RES=0x00 SYN URGP=0 OPT (0204058401010402)
To specify more chains, just ajust the log-prefix option. In the previous example DROP chain is defined.
If you use --log-prefix '[IPTABLES ACCEPT] : ' all the packets logs by this rule will be display in ACCEPT chain.
Configure the feed_db.pl script to your database settings (set corret values for the user with select and insert privileges to variables)
Install the feed_db.pl script somewhere on your firewall (for example /usr/local/bin)
Copy the init.d script called "iptablelog" in the /etc/init.d directory (if you want to start feeder automaticaly)
start the script as root (or any user that can read the iptables logs) by :
/etc/init.d/iptablelog start
Congratulations, you should be able to access to the index.php page where you have copied the web directory !
Table of Contents
This chapter gathers information about customisation of the application
If you would like to make a contribution to the FAQ, send either one of us an e-mail message with the exact text you think should be included (question and answer). With your help, this document can grow and become more useful!
This document is maintained by Gerald GARCIA <gege@gege.org>.
This FAQ is Copyright (C) 2002 by Gerald GARCIA.
Permission is granted to make and distribute verbatim copies of this manual provided the copyright notice and this permission notice are preserved on all copies.
Permission is granted to copy and distribute modified versions of this document under the conditions for verbatim copying, provided that this copyright notice is included exactly as in the original, and that the entire resulting derived work is distributed under the terms of a permission notice identical to this one.
Permission is granted to copy and distribute translations of this document into another language, under the above conditions for modified versions.
If you are intending to incorporate this document into a published work, please contact one of the maintainers, and we will make an effort to ensure that you have the most up to date information available.
There is no guarentee that this document lives up to its intended purpose. This is simply provided as a free resource. As such, the authors and maintainers of the information provided within can not make any guarentee that the information is even accurate.
These chapter is a copy of the one found in the GTK FAQ (http://www.gtk.org/faq)